stop mfa bypass
First in-browser device trust that just works
Turn your users' browsers into secure access keys with Relock's device trust engine. 100% adoption - no installs required.

stop mfa bypass
First in-browser device trust that just works
Turn your users' browsers into secure access keys with Relock's device trust engine. 100% adoption - no installs required.
device trust
device trust
Always know who to trust,
verify every request
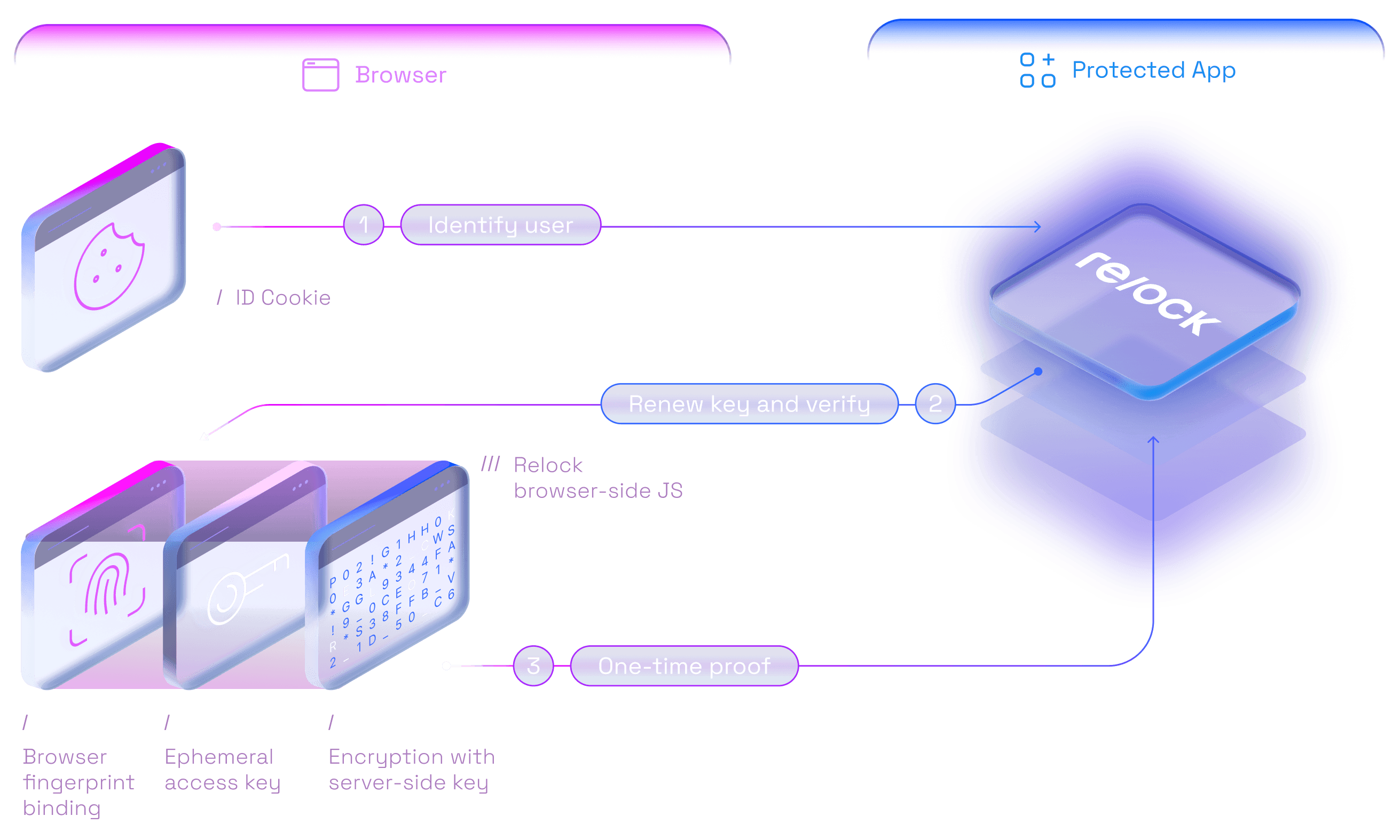


Identify: Automatically recognize users with a device-specific ID cookie that allows Relock server to decrypt user's keys.
Challenge: Renew user's access keys and issue a secure cryptographic challenge to verify if they are using a trusted device.
Verify: Receive a one-time proof that verifies the user correctly completed the challenge and can be trusted.
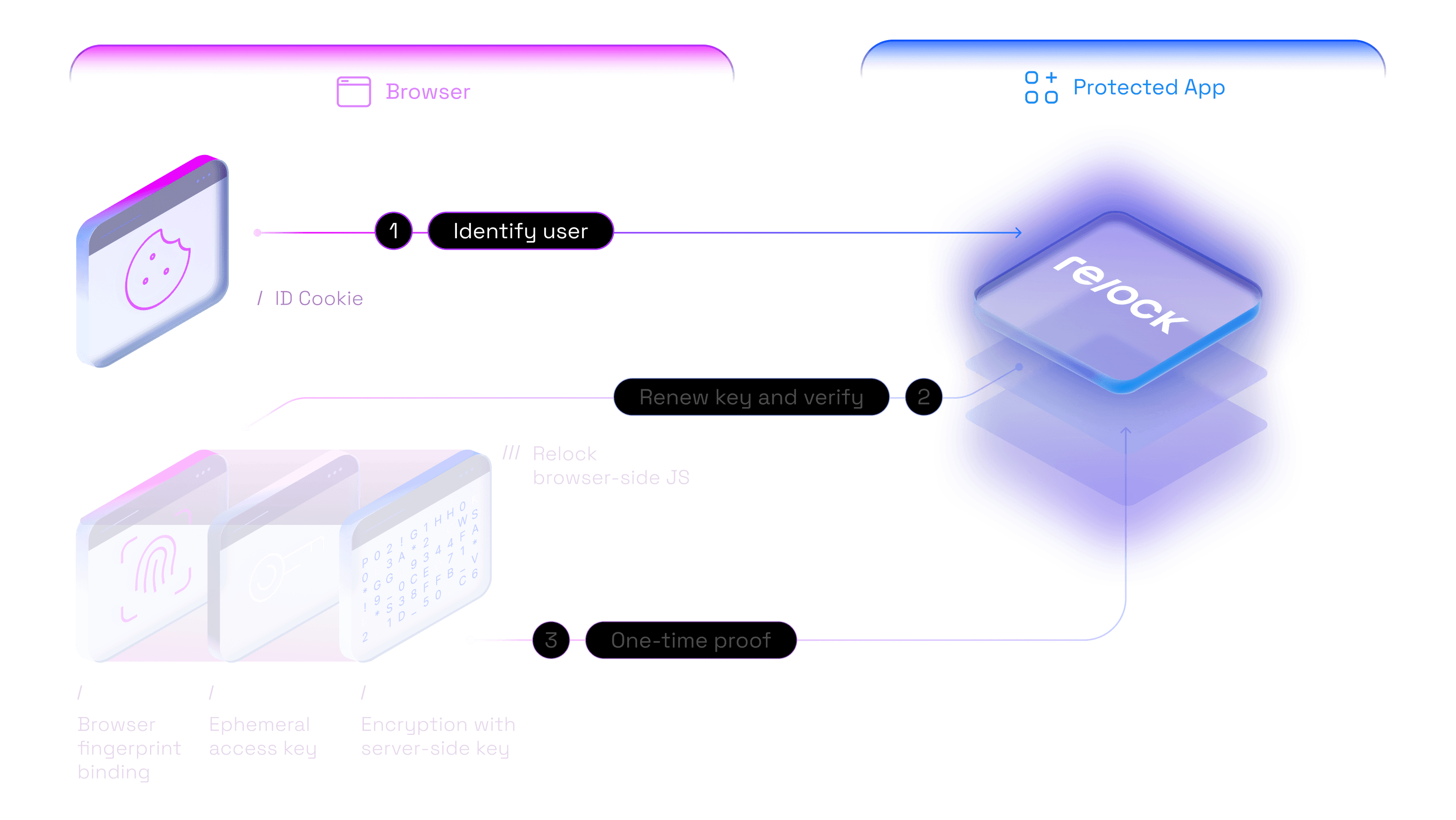
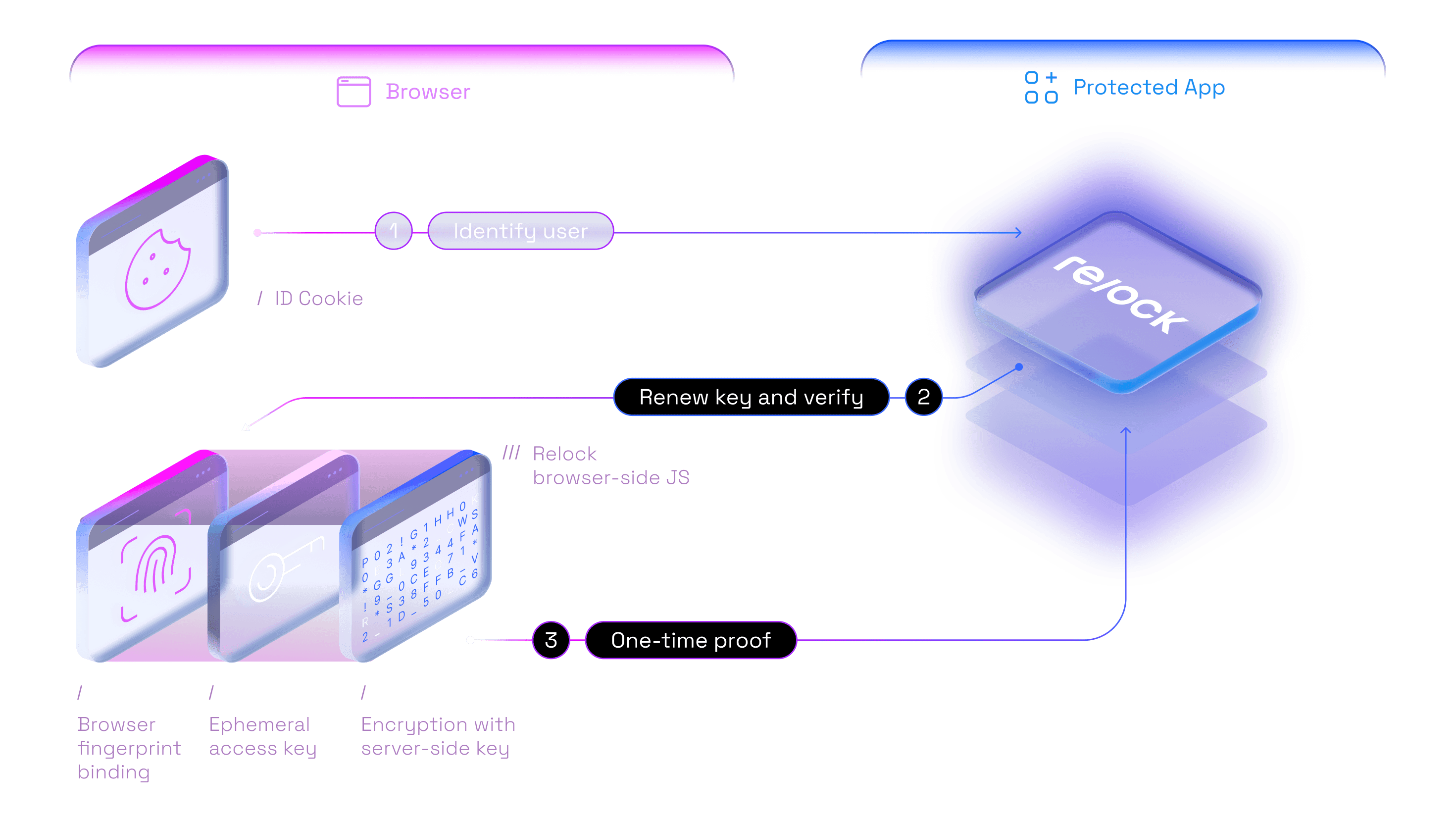
Identify: Automatically recognize users with a device-specific ID that allows Relock server to decrypt user's keys.
Challenge: Renew user's access keys and issue a secure cryptographic challenge to verify if they are using a trusted device.
Verify: Receive a one-time proof that verifies the user correctly completed the challenge and can be trusted.



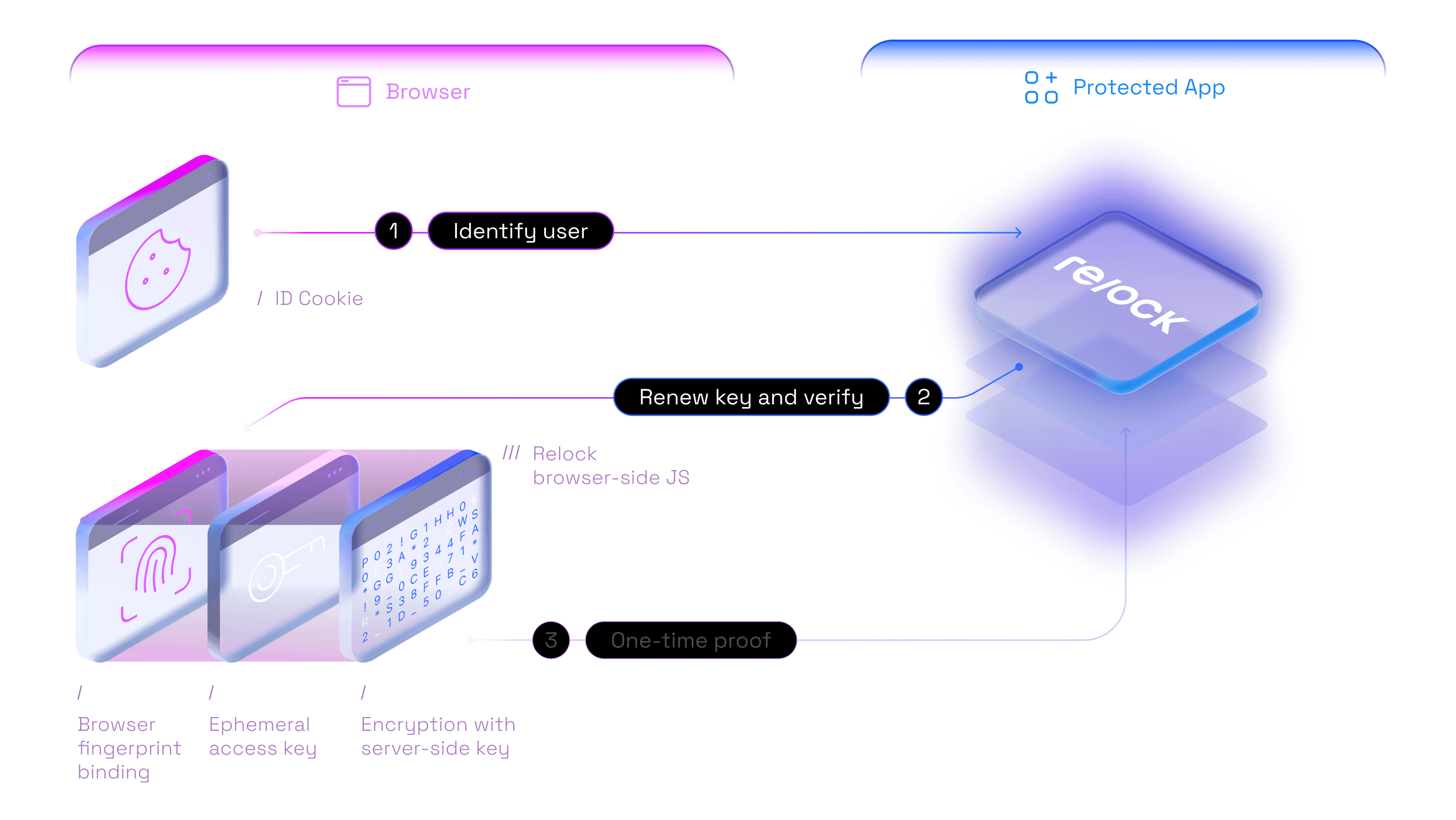
Identify: Automatically recognize users with a device-specific ID that allows Relock server to decrypt user's keys.
Challenge: Renew user's access keys and issue a secure cryptographic challenge to verify if they are using a trusted device.
Verify: Receive a one-time proof that verifies the user correctly completed the challenge and can be trusted.
Key Features
Key Features
Strong, continuous,
and fail-safe trust signal
Relock provides a persistent anchor of trust. It can be easily added to any authentication flow to stop phishing, session hijacking, and MFA bypass.
Strong, Fully Dynamic Access Keys
A patent-pending system of cryptographic keys that are verified on demand and renewed with high frequency.
Always computed, never shared
Device fingerprint- and origin-bound
Encrypted with server-side key

Strong, Fully Dynamic Access Keys
A patent-pending system of cryptographic keys that are verified on demand and renewed with high frequency.
Always computed, never shared
Device fingerprint- and origin-bound
Encrypted with server-side key

Strong, Fully Dynamic Access Keys
A patent-pending system of cryptographic keys that are verified on demand and renewed with high frequency.
Always computed, never shared
Device fingerprint- and origin-bound
Encrypted with server-side key

Continuous Authentication
In-depth defense of each session through device verification with any desired frequency
Check up to at every request
Low latency (10-100 ms)
Persistent across sessions

Continuous Authentication
In-depth defense of each session through device verification with any desired frequency
Check up to at every request
Low latency (10-100 ms)
Persistent across sessions

Continuous Authentication
In-depth defense of each session through device verification with any desired frequency
Check up to at every request
Low latency (10-100 ms)
Persistent across sessions

Inevitable Attack Detection
Even if attacked, Relock ensures inevitable and fast detection of compromised sessions
Based on clash of access keys
Impossible to circumvent
At first legitimate request

Inevitable Attack Detection
Even if attacked, Relock ensures inevitable and fast detection of compromised sessions
Based on clash of access keys
Impossible to circumvent
At first legitimate request

Inevitable Attack Detection
Even if attacked, Relock ensures inevitable and fast detection of compromised sessions
Based on clash of access keys
Impossible to circumvent
At first legitimate request

powerful use cases
powerful use cases
Works beyond guesswork in any IAM suite and flow
Relock deploys invisibly to the end user, directly into the browser.
It changes the device trust game with a clear trust / do not trust signal.


Adaptive Authentication
Solve the challenge of strong MFA adoption, fatigue, and cost with an invisible, bank-grade device trust factor. Audited for PSD2.

Adaptive Authentication
Solve the challenge of strong MFA adoption, fatigue, and cost with an invisible, bank-grade device trust factor. Audited for PSD2.
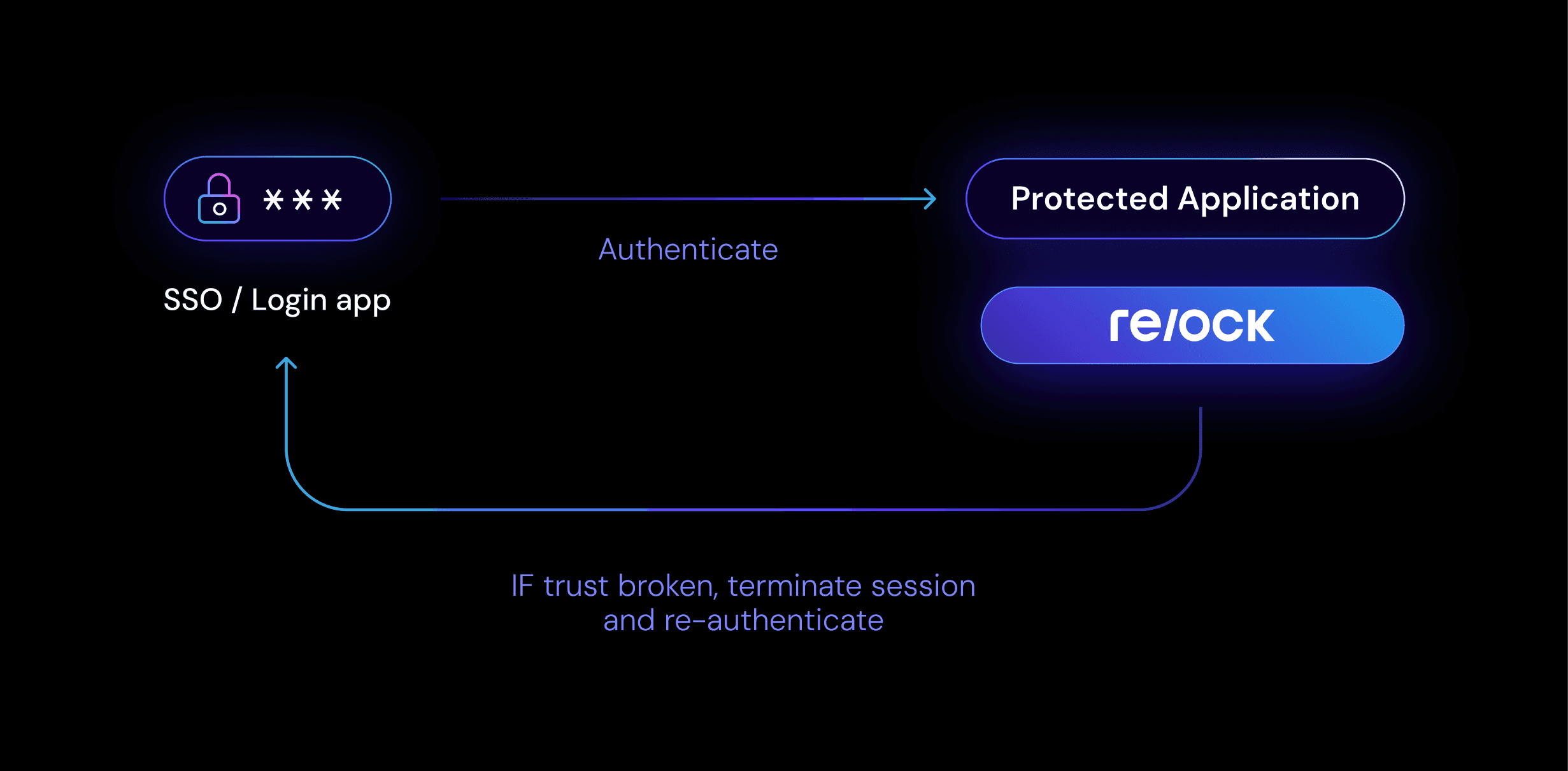

Session Protection
Add Relock continuous device verification to your application with a simple JS library and prevent the devastating MFA bypass and session hijacking attacks.

Session Protection
Add Relock continuous device verification to your application with a simple JS library and prevent the devastating MFA bypass and session hijacking attacks.

Easy integration
Seamlessly Add It
To Any Authentication



Easy integration
Seamlessly Add It
To Any Authentication
